Learn How to Find Vulnerabilities in a Website Using Burp Suite
Websites have now become majorly important for e-commerce enterprises. However, with this increased dependency on web platforms, the risk of...
Digital Forensics and Incident Response (DFIR) is an essential part of cybersecurity, focused on identification, investigation, remediation, and also providing information for legal cases or investigations. DFIR mainly has two components:
Digital Forensics: It is a subset of forensic sciences in which digital devices like computers,phones, or even cloud instances are examined to find evidence.
Incident Response: The process of containing the threat, investigating the incident, mitigating the damage, and taking steps to prevent future incidents is known as Incident response.
As a leading digital forensics service provider, Threat ResQ provides a wide range of experienced digital forensics services for our clients to assist them with their investigations. Our experts will assist you in the collection, examination, and presentation of digital evidence of the incident.
Our experts utilize industry-approved tools and methodologies to investigate and recover the systems or digital data, and we use our expertise in threat intelligence to prepare the security posture of your business to defend against future incidents.
Step 1: Detection: Our tech stack at Threat ResQ will help in the detection of the cyberattack in the quickest time possible.
Step 2: Incident Response: Our exceptional and experienced personnel will help the organizations in their immediate response to contain the threat while analyzing the event.
Step 3: Investigation: Threat ResQ’s expert digital forensics team then leads the investigation into the cyber incident, collects all the digital evidence and threat intelligence data, and does an in-depth analysis to understand the attack.
Step 4: Mitigation and Reporting: Preparing a detailed incident report while suggesting and implementing measures to prevent future attacks. The systems will be put under 24/7 monitoring to prevent the recurrence of the attacks.
Our digital forensics experts create a set of rules for examining the evidence. Every effort is made during the analysis of the evidence, to keep the original digital information safe.
Our experts carefully study the evidence on their own according to the rules and approach to make sure all the facts are correct and double-check if the evidence has been looked at properly.
A forensic report is made, which provides insight into what an expert will say. You can also ask our experts to prepare a direct examination for yourself and a cross-examination for an opposing expert.






Digital forensics is a critical aspect of today’s case law. In some instances, if the evidence is not asked for correctly with the proper technical terminology, or if someone does not properly understand how to access the evidence, receiving incorrect information or nothing at all will be the outcome.
As a result of the increased use of computers in all arenas of life, forensic software and hardware have been developed to assist and guide law enforcement officials. This may be in the form of determining if the system has been compromised or monitoring the activities of data on an electronic device.
Proposals and agreements should be drafted before work can even begin. Our digital forensics experts will draft a protocol for examination of the evidence. This protocol will ensure that all parties involved continue to work under these terms and conditions. Every effort is made during an analysis to preserve the original digital information.
Our experts use a thorough, independent analysis of the evidence to ensure that all facts are accurate and to determine if evidence has been properly analyzed. As with any situation, there will always be some potential errors in conclusions drawn due to human error.
Every case is treated as if it were going to trial by our experts.
A forensic report provides insight into what an expert will say. You can also ask our experts to prepare a direct examination for yourself and a cross-examination for an opposing expert.





As part of a forensic investigation, a series of events occur. Among these events are:
Digital Forensics Consultation: A subject matter expert in digital forensics will work together with you to determine what information needs to be collected, ensure that the correct tools are used, and provide insight into a wide range of issues from preservation concerns to data analysis and reporting.
Digital Forensics Acquisition: During the acquisition phase, we’ll work with you to track down every last bit of information that can help your case. We stay in constant contact and update you regularly.
Our experts make forensic images and copies of computers, servers, cell phones, cloud data, and/or social media using on-site collections.
Digital Forensics Analysis: In addition to recovering deleted data, our experts examine the data using specialized forensic technology and methods. With our in-depth analysis, we aim to understand what happened, how it happened, and who could be liable.
Analyzing the data enables us to answer questions such as::













Digital Forensics Reporting
In this stage, the technical explanation of what transpired in a case is set out. This report would include an explanation and analysis of forensic artefacts that point toward proof of user attribution, for instance, if there were suspicions that a former employee had stolen intellectual property. Specifically, what files were accessed, how they were removed from the organisation, who took the data when it was stolen, and what possible uses they may have.
Digital Forensics Expert Testimony
An expert in digital forensics must first be qualified before they can testify in court. If the expert's credentials are contested, the lawyer who retained the expert must provide evidence that the expert has the required educational and professional background. These inquiries cover matters such as the expert's training, credentials, case experience, and specialised knowledge. A specialist must also communicate difficult technical issues in simple terms in order to be effective. Our experts are adept at explaining technology in a way that fact-finders in a case can understand.
Discover Threat ResQ's advanced technology and highly skilled professionals who work to safeguard your digital assets and maintain compliance with our digital forensic services.









In today's digital age, protecting your organization's digital assets and ensuring compliance is crucial. Don't leave the security of your digital assets to chance, trust Threat ResQ to provide you with the highest level of protection.




















Read articles and actively engage in conversations about digital forensic services to learn best practices and gain insight into trends that are shaping security today.
Websites have now become majorly important for e-commerce enterprises. However, with this increased dependency on web platforms, the risk of...
Insider threats pose a significant risk to organizations, as malicious or negligent insiders can cause significant damage to critical data...
As organizations increasingly embrace cloud computing, ensuring strong cloud security has become a priority. In this blog, we explore best...








At Threat ResQ, we understand the importance of customer satisfaction, which is why we go above and beyond to ensure our clients' needs are met. We pride ourselves on delivering top-notch services and strive to exceed our clients' expectations every time.
Threat ResQ has been a pleasure to work with and they have been very helpful in helping us resolve all the vulnerabilities and issues we came across while doing our app development. Their VAPT services are worth every penny spent on them.





We have been working with Threat ResQ for a while now, and we've been very impressed with the service they've provided. The team is very responsive and proactive - the way we like it. We look forward to working with them on all our future projects.





We were able to save a lot of money and time while they were working on the project. They have a very proactive team who is ready to help out with any queries that we have regarding cybersecurity. We would definitely like to work with them again. Thanks!











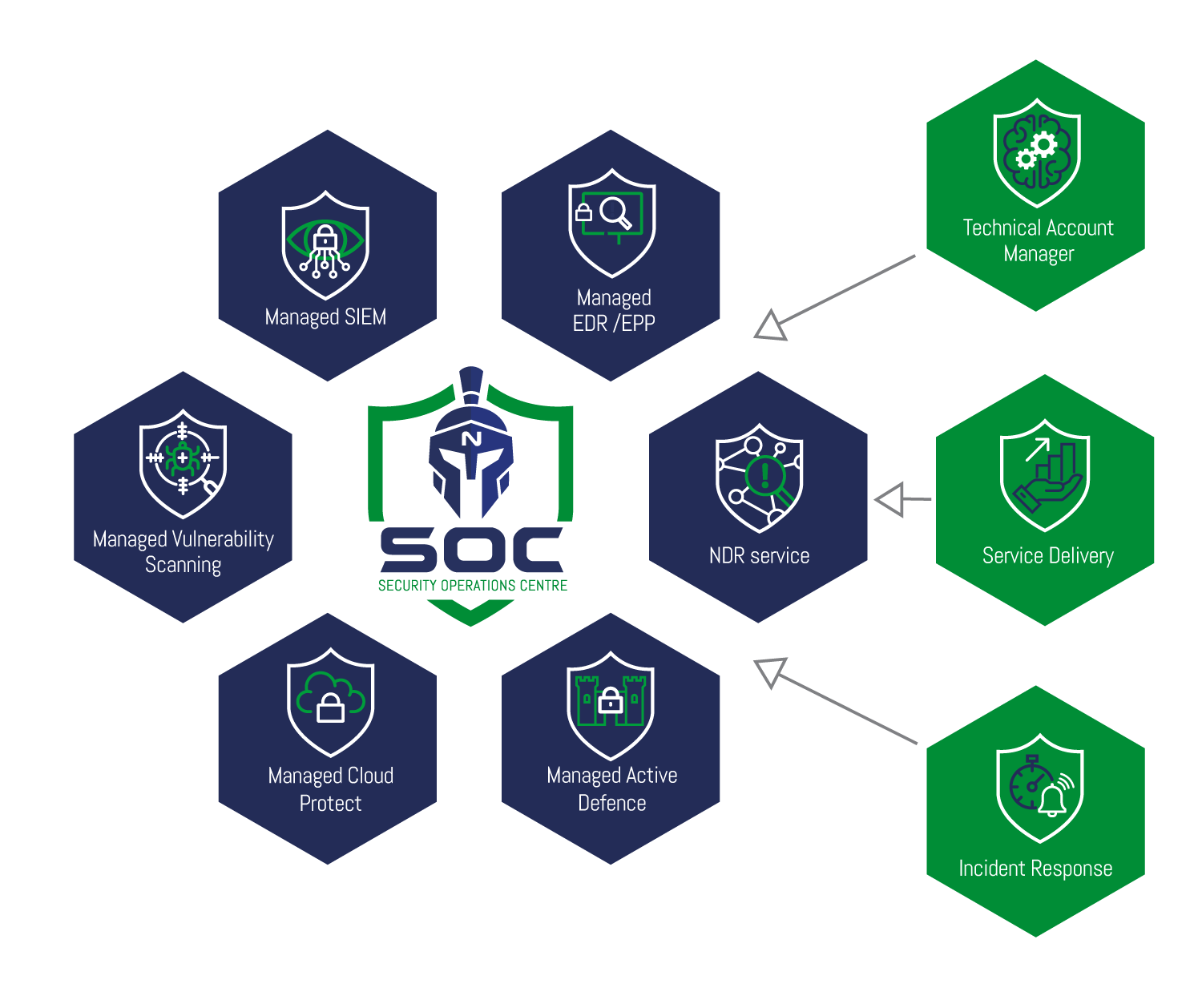
Digital forensic cybersecurity services may include incident response, threat intelligence, malware analysis, network forensics, data recovery, forensic analysis, and legal support.
SOC team will be there for you 24/7 to prevent security breaches, warn you about any potential Vulnerabilities, and fix them before they turn into problems.
Digital forensic services are necessary for organizations because they help to:
Investigate security incidents: Digital forensics can help organizations identify and respond to security incidents, such as data breaches, malware infections, and insider threats.
Preserve evidence: Digital forensics can help organizations preserve digital evidence that may be needed for legal proceedings, regulatory compliance, or internal investigations.
Recover lost data: Digital forensics can help organizations recover lost or deleted data from digital devices, such as hard drives, smartphones, and tablets.
Monitor employee activity: Digital forensics can help organizations monitor employee activity to detect policy violations, intellectual property theft, and other insider threats.
Mitigate risk: Digital forensics can help organizations identify and mitigate risks to their digital assets, such as vulnerabilities in their IT systems or weaknesses in their cybersecurity policies.
Organizations can find a reputable digital forensics provider by:
Researching the provider’s reputation: Look for reviews, testimonials, and case studies from other organizations that have used the provider’s services.
Checking the provider’s credentials: Look for providers that are certified in digital forensics and have experience working with organizations similar to yours.
Reviewing the provider’s service offerings: Look for providers that offer a range of digital forensic services to meet your organization’s needs.
Evaluating the provider’s customer service: Look for providers that are responsive, communicate clearly, and provide ongoing support to their clients.
Verifying the provider’s security protocols: Look for providers that have strong security protocols in place to protect your organization’s sensitive data.
Organizations can prepare for a digital forensic investigation by implementing appropriate policies and procedures for data collection and preservation, as well as incident response. This may include developing an incident response plan, conducting regular data backups, and ensuring that employees are trained in data security best practices. It's also important for organizations to work with their digital forensic services provider to understand the investigation process and ensure that they are providing the necessary access and resources to facilitate the investigation.

