- Join our company
- Email: info@threatresq.com
- Phone: (+91) 9910016361














Websites have now become majorly important for e-commerce enterprises. However, with this increased dependency on web platforms, the risk of cyber threats has also increased for such enterprises.
A website vulnerability refers to a weakness within the code of the website or web application. Web vulnerabilities are exploited by attackers, through which they can get unauthorized access to critical data and assets on the website.
From understanding common vulnerabilities to implementing robust security measures, ThreatResQ helps you shield your e-commerce platforms from potential risks.
Examples of website vulnerabilities include Insecure Direct Object References (IDOR), which may allow unauthorized access to sensitive data, SQL Injection attacks can help manipulate databases and their content.
Cross-site Scripting attacks, which allow attackers to inject malicious scripts into web pages, Broken authentication may result in unauthorized user account access, any authenticated functionality, etc.
Using components with known vulnerabilities may allow attackers to exploit any potential CVE not patched in the web application.



Through conducting website vulnerability analysis, you can avoid data breaches, financial losses, and damage to an enterprise’s reputation. It builds trust in your brand when you make sure about the safety of customers’ sensitive information, like personal and payment details.
Web app vulnerabilities specifically can lead businesses to severely bad consequences, which could be data breaches, unauthorized account access, DDoS, Remote Code execution, etc.
While conducting various website security assessments for E-commerce enterprises and others, ThreatResQ’s team curated a list of the most common Web Application vulnerabilities that we came across during the assessment. Such vulnerabilities are exploited in the wild in web applications and should be given more attention.



Top 4 common website vulnerabilities according to ThreatResQ’s VAPT assessments of web applications:


Cross-Site Scripting (XSS) is a well-known web vulnerability that allows an attacker to inject malicious scripts into web applications. Such scripts then get executed whenever a general or targeted victim accesses the web page with the injected script. The impact of XSS can be severe, as it can allow attackers to steal sensitive user data, session cookies, etc.
Here’s how it works:



SQL injection is another type of vulnerability where attackers manipulate input fields to execute malicious SQL queries on a website’s database. This occurs when a website fails to properly validate and sanitize user input, tricking the website’s database into executing commands given by the attacker.
Such a vulnerability enables attackers to view, modify, or even delete the sensitive data in the backend database of the website.
Here’s how it works:
Parameter tampering, also known as query string manipulation, is a website vulnerability where attackers modify the values in the URL parameters or form fields to manipulate the website’s logic or behavior.
Such vulnerabilities can be used to change product prices, apply unauthorized discounts, or bypass payment processes, leading to financial losses for e-commerce businesses.
Here’s how it works:
If an application depends greatly on client-side validation or fails to validate user input on the server-side during the application workflow, it becomes vulnerable to price manipulation or parameter tampering attacks.
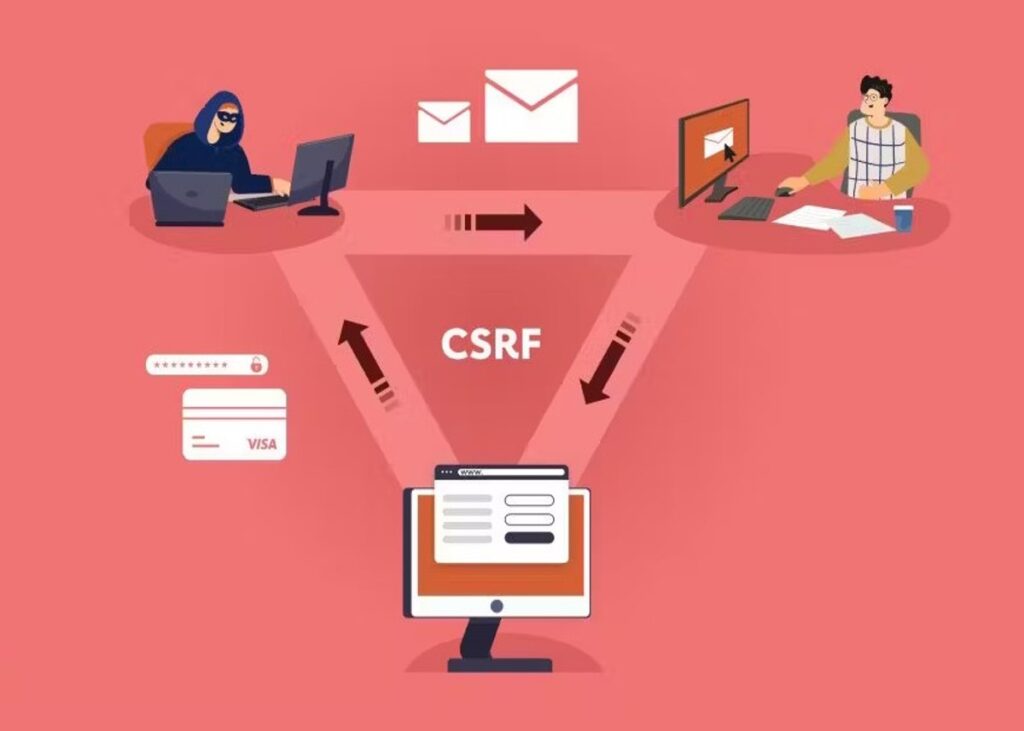


Cross-site request forgery (CSRF) is a well-known vulnerability where attackers trick a user’s web browser to send unauthorized requests to a separate web application where the user is authenticated or logged in. The core cause of this web vulnerability is not validating the origin of the incoming requests appropriately.
The success of such attacks depends on exploiting human vulnerabilities through social engineering attacks like phishing. The ultimate aim of the attacker is to trick the user into accessing a malicious website and executing the exploit. The attack succeeds because the modified request to a legitimate application automatically contains the user’s cookies.
Here’s how it works:
There are automated website vulnerability scanning systems or tools that can detect potential vulnerabilities or weaknesses in a web application. Such tools help with faster security assessments with good results. Examples of automated website vulnerability scanning tools are Nessus, BurpSuite, Caido, Qualys, OpenVAS, Detectify, etc.
The company’s security team should utilize such automated tools for regular security checkups. To ensure comprehensive protection, companies should also make sure that the manual assessments are done timely and accurately to not miss any severe vulnerabilities or identify any false positives by automated tools, striking the right balance between both manual and automated approaches.
1. Keeping Software and Plugins Updated: A website’s software, content management system (CMS), and plugins should always be updated to the latest security patches for vulnerability prevention. These security patch updates have the known vulnerabilities patched.
2. Input Validation and Sanitization: Developers should Implement strong input validation and sanitization techniques that are essential to blocking common attacks like SQL Injection and XSS. When an application Validates and sanitizes user input, it makes sure that only expected and safe data is approved and processed by the website, mitigating the risk of malicious code injection.
3. Web Application Firewalls (WAFs): A Web Application Firewall (WAF) should be implemented, which toughens your security posture by introducing an additional layer against a wide range of web-based vulnerabilities. A WAF can intercept and filter incoming web traffic through predefined filters and regexes, identifying and blocking malicious requests before they reach the web server.
4. Regular Security Audits and Threat Intelligence: There should be periodic security audits on the application to identify potential vulnerabilities and weaknesses in the website’s security posture. Such periodic audits can be scheduled every week, month, or quarterly. Also, Doing Threat intelligence alongside security audits can be beneficial as you can analyze the threat intelligence data and feeds from reputable resources, which can help the security teams stay ahead of emerging threats.
5. Running a Bug Bounty Program: Web applications should implement a bug bounty program encouraging independent security researchers to find and report website vulnerabilities. This can help enhance your website’s security and nurture a collaborative approach to cyber defense.