- Join our company
- Email: info@threatresq.com
- Phone: (+91) 9910016361













In today’s world, where the threat landscape is evolving, organizations are adopting proactive approaches to cybersecurity. One smart way that organizations are using to strengthen their defense is through threat intelligence.
In this blog, we’ll talk about the role threat intelligence plays in defense and how ThreatResQ leverages it to help organizations. Threat intelligence can help organizations stay ahead of cyber threats, which can enhance their cybersecurity posture and defend their critical digital assets.



Threat Intelligence involves the collection, analysis, and dissemination of information about potential cyber threats. Threat intelligence research is a way to predict and understand potential cyber threats before they even occur, for better action plans and defenses. It’s like having a crystal ball for cybersecurity.
ThreatResQ understands how important it is to be actively ready for cyber threats. That’s why we utilize advanced threat intelligence to gather data on cyber trends, threats, and vulnerabilities. This helps organizations prepare and avoid potential threats before they harm their systems and data.



ThreatResQ’s threat intelligence solutions let organizations know what kinds of cyber threats are out there and how they can prevent them. By analyzing a wide range of data sources, including dark web forums, security feeds, and incident reports, ThreatResQ identifies indicators of compromise and emerging attack patterns.
Threat intelligence research helps in strategic decisions such as resource allocation, technology investments, risk management strategies, etc. ThreatResQ’s comprehensive threat intelligence solutions help decision-makers understand the Threat scenario and make informed decisions accordingly for their organizations.
Organizations with up-to-date threat intelligence can improve and implement better incident response efforts. By continuously analyzing emerging trends, and updating threat intelligence feeds, It enables quick identification of the nature of an attack, its source, and the impact it can cause. This allows organizations to come up with better defensive and recovery plans.
ThreatResQ gets it – every organization has its own cybersecurity needs, so they will need tailored threat intelligence research that is mostly relevant to their needs. ThreatResQ provides tailored threat intelligence solutions that can help organizations prioritize what they really need.
This way, they can protect their operations by focusing on mitigating risks that are most relevant to their industry.
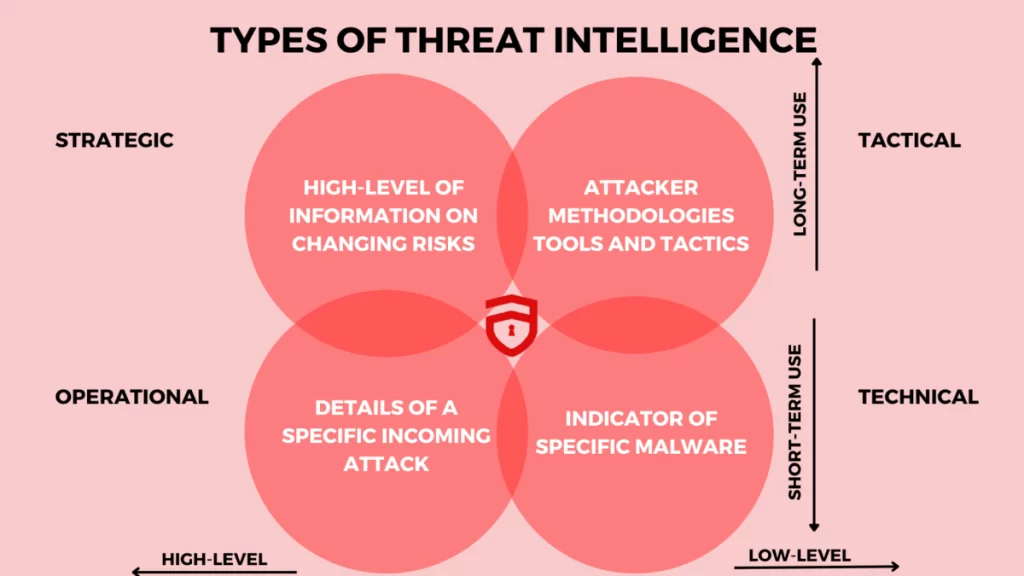


This type of intelligence includes high-level intelligence feeds that help the top bosses, like CEOs, CISOs, managers, etc., make business decisions. This kind of intelligence is prepared for a non-technical audience and includes the latest and major trends, possible risks, etc. With such information, organizations can make strategic decisions and policies for tackling risks.
Tactical intelligence is more precise and technical in nature. Such intelligence helps in identifying indicators of compromise (IOCs), such as vulnerable URLs, Ip addresses, malicious files, unusual traffic, etc. This helps technical security analyst teams analyze what techniques, tools, and attacks are in trend among threat actors at the moment.
Operational intelligence is all about answering the questions – “Why? How? Who?”. It contains thorough information about past attacks, such as the intent behind the attack, tools used, procedures carried, etc. This requires more resources than Tactical intelligence and has a longer useful life because Threat actors can’t change their TTPs, i.e., Tactics, techniques, and procedures, even if they change their tools.
Such information is collected through online discussion communities or by the attackers themselves, which is hard.
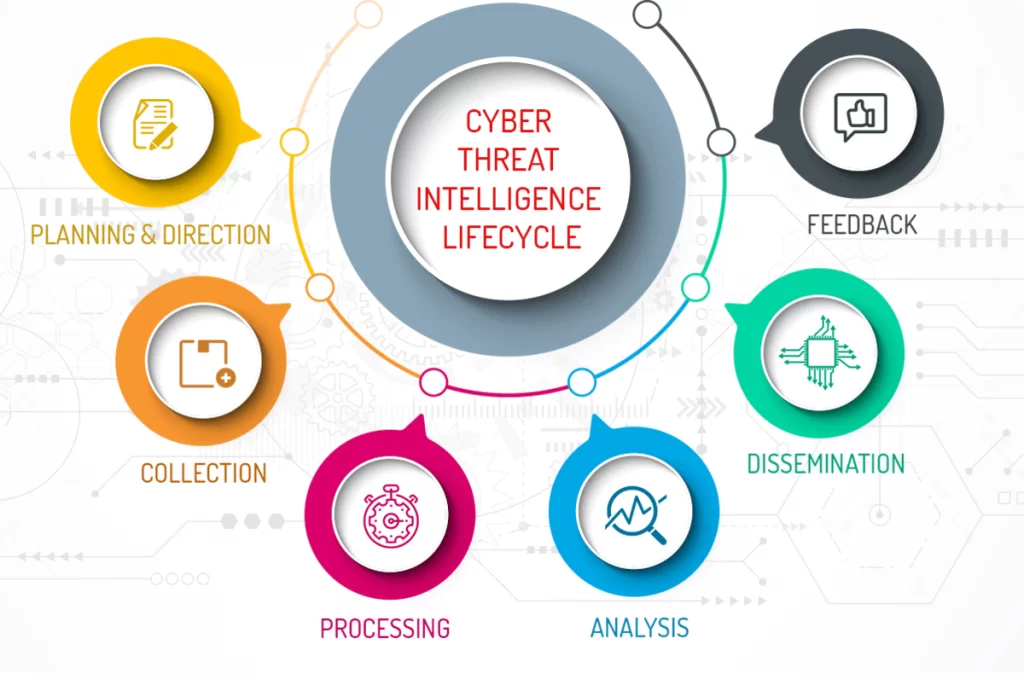


The threat intelligence lifecycle is a step-by-step process that organizations go through to utilize the raw data for intelligence purposes and strengthen their cybersecurity defenses.
This whole cycle is made up of six steps, which are followed in a loop through feedback for better response at the end of each cycle. These six steps are as follows:
This is where you do the planning and define the requirements needed for a threat intelligence operation. In other words, We are preparing a roadmap for the operation.
This includes:
In the second step, the teams start gathering relevant information through various sources. Such sources can include Open source intelligence, commercial threat feeds, communities, news, blogs, dark web monitoring, internal logs, etc.
The collected data in the second stage is the raw data at this point. In the third step, the collected raw data is processed into a suitable and readable format for analysis. Such raw data is also checked for false positives and filtered according to the needs of the threat intelligence program. ThreatresQ implements AI based solutions and human resources for the best processing results.
At this step, the processed data is now truly analyzed for finding answers and information about the threat intelligence program for communication with the stakeholders. This further influences the organization’s decision-making regarding security policies or implementations. This analysis answers questions about:
Dissemination is the step where the Threat intelligence team conveys all the information and their insights after the analysis to stakeholders, Security analysts, or any other organizational party.
Threat intelligence teams prepare a thorough report about all of the analysis done and intelligence feeds collected. Such reports should be to the point and less technical for better understanding by stakeholders and other teams.
As told earlier in the blog, this life cycle is iterative, i.e., followed in a loop. In this final step, Threat intelligence teams are provided with feedback on the report provided to them. It’s like reviewing how well you did the task and learning for the next program.
This can improve future threat intelligence programs for better results. Stakeholders or other teams can also give feedback on how well they were able to get through the report and if there are any improvements to make.
Threat intelligence plays a vital role in building effective cyber defense strategies. With ThreatResQ’s advanced threat intelligence solutions, organizations can be updated about trending cyber threats and vulnerabilities, have better incident response times, and do continuous monitoring of their networks.
By leveraging threat intelligence, organizations can enhance their cybersecurity posture, mitigate risks, and stay ahead of threat actors. Empower your organization with ThreatResQ’s comprehensive threat intelligence solutions now!